State-supported cyber attackers with links to China’s Ministry of State Security have reportedly aimed their sights on multiple sectors in 17 nations, ranging from North America to Europe and Asia, as revealed in a fresh analysis.
The latest findings come from cyber intelligence firm, Recorded Future’s Insikt Group, which has been closely observing the activities of RedHotel, a cyber-espionage group with connections to China. This group, known to Microsoft as Charcoal Typhoon and identified as BRONZE UNIVERSITY by SecureWorks, is marked for its wide-ranging targets.
Jon Condra, who heads strategic threat analysis at Recorded Future, shared insights on RedHotel’s vast operations. “These hackers are among the top-tier of Chinese-supported cyber groups that we’ve observed. They’ve breached a U.S. state legislature, accessed tech R&D data, and even sought out COVID-19 related research,” he noted.
The group, believed to be operating primarily out of Chengdu, has expanded its focus beyond Southeast Asian governments, venturing into sectors like academia, media, and telecommunications.
RedHotel, as the report indicates, leverages an advanced arsenal of malware and techniques, showing similarities with other noted Chinese Advanced Persistent Threat (APT) factions, such as APT41. With Chengdu emerging as a hotspot for such activities, the nexus between APTs and local academic institutions has become increasingly apparent.
The primary objectives driving these cyber-espionage activities seem to be intelligence accumulation and economic spying. Besides the previously noted breach of a U.S. state legislature, RedHotel has also focused on COVID-19 studies and tech outfits.
Using a mixture of known malware strains like ShadowPad and Winnti, and their unique tools like Spyder and FunnySwitch, their tactics often blur lines, making attribution challenging.
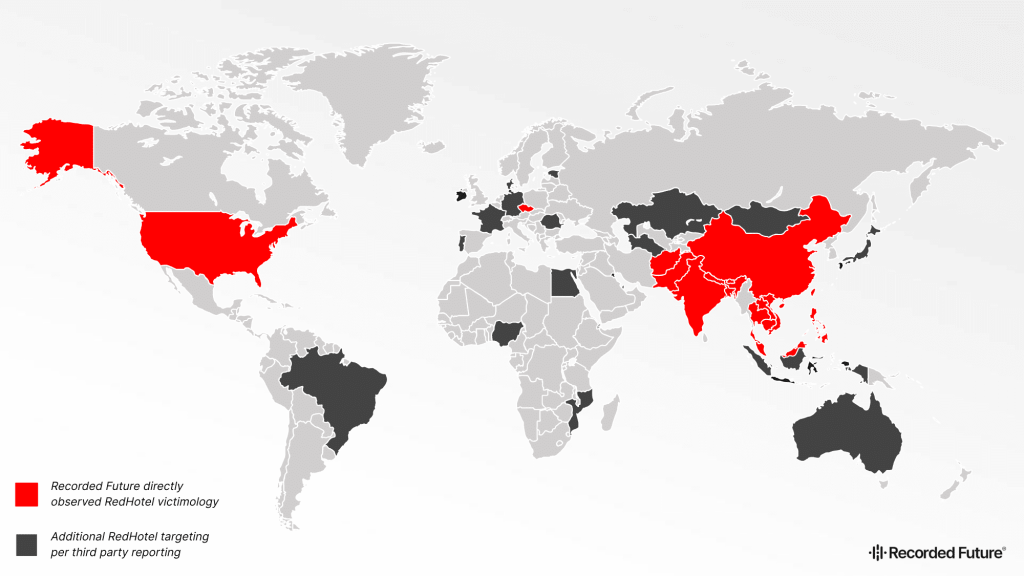
The report further reveals a vast geographical footprint of their victims, encompassing countries such as Afghanistan, the Czech Republic, Hong Kong, Malaysia, Palestine, Taiwan, and the U.S. Most targets in these countries tend to be governmental bodies, from PM offices to interior departments.
Moreover, RedHotel’s operations extend to niche areas, such as Taiwanese research hubs, Hong Kong’s pro-democracy groups, and even online betting platforms.
Citing a 2022 study by PWC, the report underscores RedHotel’s prominence as the standout Chinese threat actor of that year.
RedHotel’s modus operandi hinges on two phases – an initial breach followed by establishing enduring access within the infiltrated system. Notably, from 2019-2023, they employed tools disguised as Microsoft Windows’ Compatibility Troubleshooter service.
Tracking the group’s cyber trail, Insikt Group pinpointed over 100 IP addresses associated with RedHotel between 2022 and 2023. The cyber group frequently repurposes compromised infrastructure for subsequent breaches, an evolving pattern that showcases their adaptability.
Recent reports have drawn attention to China’s expansive hacking campaigns, with hints pointing towards a surge in cyber activities aligned with the nation’s military objectives.
Key U.S. sources recently shared with The New York Times about potentially harmful Chinese malware found on infrastructure linked to U.S. military facilities. Meanwhile, the Washington Post shed light on China’s far-reaching access within the upper echelons of the Japanese government.
The Insikt Group report underscores the unwavering nature of RedHotel’s operations, even in the face of public exposure. “Their adaptability and vast toolkit make them a formidable actor. Given past trends, we foresee no slowdown in their activities,” the report concluded.
Note: Corrections were made to a prior version of this article regarding China’s Ministry of State Security’s classification. It is a civilian intelligence organization.
Found this news interesting? Follow us on Twitter and Telegram to read more exclusive content we post.


