Telecom operators in the Middle East face a rising cyber threat, as malevolent actors employ the newly discovered HTTPSnoop and PipeSnoop malware tools to remotely manipulate infected systems.
HTTPSnoop operates by interacting with Windows HTTP core drivers and devices, executing specific content upon detecting particular HTTP(S) URLs. On the other hand, PipeSnoop waits to receive and run arbitrary shellcode from a designated pipe.
Cisco Talos, in its comprehensive report, reveals that both these tools are part of the ‘ShroudedSnooper’ cyber-espionage toolkit, though they cater to distinct tactical requirements based on infiltration depth.
Astonishingly, both malware tools masquerade as part of Palo Alto Networks Cortex XDR’s security modules, a tactic to remain unnoticed.
Deep Dive: HTTPSnoop
By tapping into rudimentary Windows APIs, HTTPSnoop keeps an eye on HTTP(S) traffic, waiting to catch predefined URLs. When it detects these URLs, it swiftly deciphers incoming base64-encoded data, subsequently running it as shellcode on the breached system.
Employing DLL hijacking, the malware becomes operational on the target machine and bifurcates into two sections: one that constructs a concealed web server using kernel calls, and the other, its configuration.
Setting up an incessant monitoring loop, HTTPSnoop stands by for incoming HTTP requests. Upon obtaining validated data, it processes it; otherwise, it responds with an HTTP 302 redirect.
The malware then decrypts and runs the received shellcode, and sends back the outcome to the perpetrators in the form of base64-encoded XOR-encoded segments.
Furthermore, it checks to avoid any URL overlap with previously set server URLs.
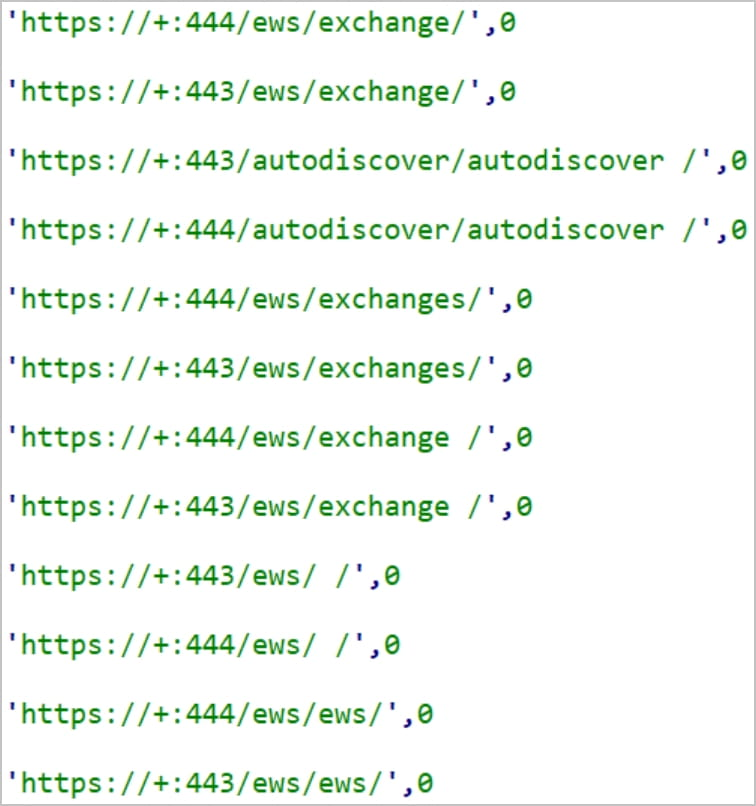
Over a span of twelve days in April 2023, three HTTPSnoop iterations emerged, each showcasing varied URL detection methods. The most recent version is finely tuned to catch fewer URLs, optimizing its concealment capabilities.
Crafting URLs resembling genuine Microsoft Exchange Web Services and OfficeTrack requests ensures that these malicious demands are camouflaged amidst regular traffic.
Spotlight: PipeSnoop
In May 2023, Cisco flagged PipeSnoop, a tool that functions as a gateway, running shellcode operations on invaded systems via Windows IPC channels.
Interestingly, while HTTPSnoop zeroes in on externally accessible servers, PipeSnoop thrives in the heart of compromised networks.
Although PipeSnoop relies on an external module for its shellcode, Cisco analysts are yet to pin it down.
Owing to their strategic importance in managing vital infrastructure and transmitting confidential data, telecom service providers remain in the crosshairs of government-backed cyber adversaries. The escalating assaults on telecom bodies emphasize the pressing need for heightened security protocols and global collaborations to shield these entities.
Found this news interesting? Follow us on Twitter and Telegram to read more exclusive content we post.


