Computer Hacker Working in Dark Room
In a startling development, a highly advanced backdoor malware dubbed ‘Deadglyph’ has emerged, wreaking havoc in a cyberespionage campaign against a government agency located in the Middle East.
Attributed to the notorious hacking group Stealth Falcon APT, also known as Project Raven or FruityArmor, this state-sponsored hacking collective hails from the United Arab Emirates (UAE) and has a long history of targeting activists, journalists, and dissidents over nearly a decade.
At the recent LABScon cybersecurity conference, Filip Jurčacko, a researcher at ESET, unveiled an in-depth analysis of the newly discovered modular malware and elucidated its methods for infiltrating Windows devices.
The Mechanics of Deadglyph
ESET’s research has not yet uncovered the initial infection vector, although it is suspected that a malicious executable, possibly masquerading as a program installer, serves as the point of entry.
Nevertheless, ESET has meticulously dissected the components of Deadglyph’s infection chain to provide a comprehensive understanding of its operation and its tactics to elude detection.
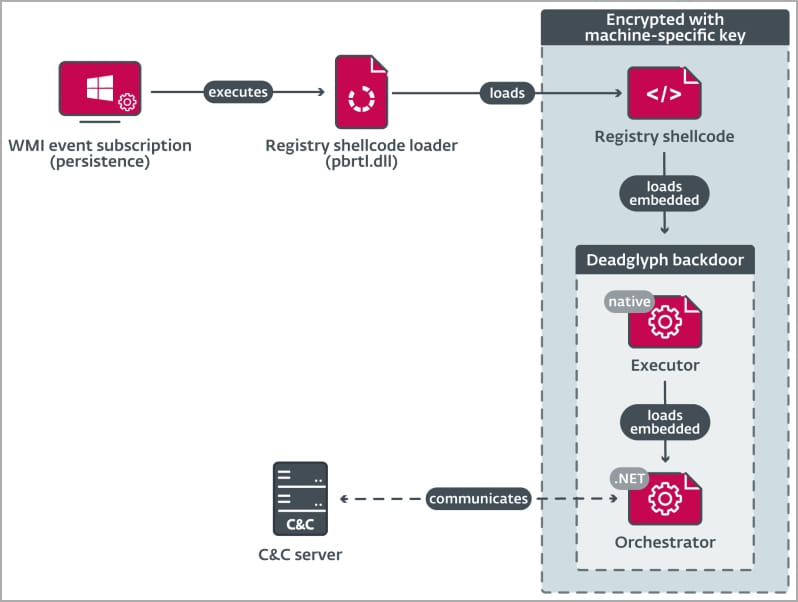
The Deadglyph loading process commences with a registry shellcode loader (DLL) that extracts code from the Windows registry to introduce the Executor (x64) component, which subsequently initializes the Orchestrator (.NET) component.
Remarkably, only the initial component is stored as a DLL file on the compromised system’s disk, thereby minimizing the chances of detection. The loader extracts the shellcode from the Windows Registry, encrypting it to increase the complexity of analysis.
To further obfuscate its presence, the threat actors behind Deadglyph employed a homoglyph attack within the VERSIONINFO resource, utilizing distinct Greek and Cyrillic Unicode characters to mimic Microsoft’s information, creating the illusion of a legitimate Windows file.
ESET’s report elucidates this tactic, stating, “We spotted a homoglyph attack mimicking Microsoft Corporation in the VERSIONINFO resource of this and other PE components. This method employs distinct Unicode characters that appear visually similar, but in this case not identical, to the original characters, specifically Greek Capital Letter San (U+03FA, Ϻ) and Cyrillic Small Letter O (U+043E, о) in Ϻicrоsоft Corpоratiоn.”
The Executor component takes charge of loading AES-encrypted configurations for the backdoor, initializes the .NET runtime, loads the .NET portion of the backdoor, and functions as its library. Finally, the Orchestrator is responsible for communication with the command and control server (C2), employing two modules named ‘Timer’ and ‘Network.’
In the event of a failure to establish communication with the C2 server within a specified timeframe, Deadglyph activates a self-removal mechanism, preventing analysis by cybersecurity researchers and experts.
The Modular Nature of Deadglyph
One distinctive feature of Deadglyph is its modularity, enabling it to download new modules from the C2 server that contain various shell codes executed by the Executor component. This modular approach allows threat actors to craft customized attacks, pushing them to victims to execute additional malicious functions.
These modules are equipped with both Windows and custom Executor APIs. The latter includes 39 functions, enabling operations such as file manipulation, executable loading, Token Impersonation, and encryption and hashing.
Although ESET has identified only a fraction of Deadglyph’s potential modules, it has identified three: a process creator, an information collector, and a file reader.
The information collector employs WMI queries to provide the Orchestrator with a wide range of system information, including details about the operating system, network adapters, installed software, drives, services, drivers, processes, users, environment variables, and security software.
The process creator is a command execution tool that executes specified commands as new processes and relays the results to the Orchestrator. Meanwhile, the file reader module reads and transmits file contents to the Orchestrator, with an option for operators to delete files after retrieval.
Despite only scratching the surface of Deadglyph’s capabilities, ESET’s findings underscore the severity of the threat posed by Stealth Falcon’s creation. As the initial infection method remains unknown, crafting specific defense strategies against the malware remains a challenge. For the time being, defenders can rely on the indicators of compromise (IoCs) outlined in ESET’s report.
Related Articles:
- Hackers Infiltrate Telecom Providers Using Novel HTTPSnoop Malware
- Iranian Hackers Employ ‘Sponsor’ Malware to Backdoor 34 Organizations
- FBI Successfully Eliminates Qakbot Malware from Infected Windows PCs
- New Malware Targets Business Routers for Data Theft and Surveillance
- CISA Raises Alarm Over New ‘Whirlpool’ Backdoor in Barracuda ESG Attacks


