In a recent cyber espionage campaign, the threat actors, allegedly linked to the group known as Patchwork, are observed to be targeting Chinese universities and research institutions. KnownSec 404 Team has reported this activity, noting the deployment of a backdoor, codenamed EyeShell.
Patchwork, also recognized as Operation Hangover and Zinc Emerson, is believed to be an Indian-backed cyber threat group. Active since at least December 2015, the group’s operations are usually narrowly focused, primarily targeting Pakistan and China with custom implants such as BADNEWS through spear-phishing and watering hole attacks.
The group has been linked with cyber-espionage entities with an Indian connection, including SideWinder and the DoNot Team, based on overlapping tactics.
Earlier in May, Meta identified and disabled 50 Patchwork-operated accounts on Facebook and Instagram. The group leveraged rogue messaging apps on the Google Play Store to harvest data from users in Pakistan, India, Bangladesh, Sri Lanka, Tibet, and China.
“Patchwork deployed a series of sophisticated fake personas to socially engineer users into clicking on malicious links and downloading harmful apps,” Meta commented on the issue.
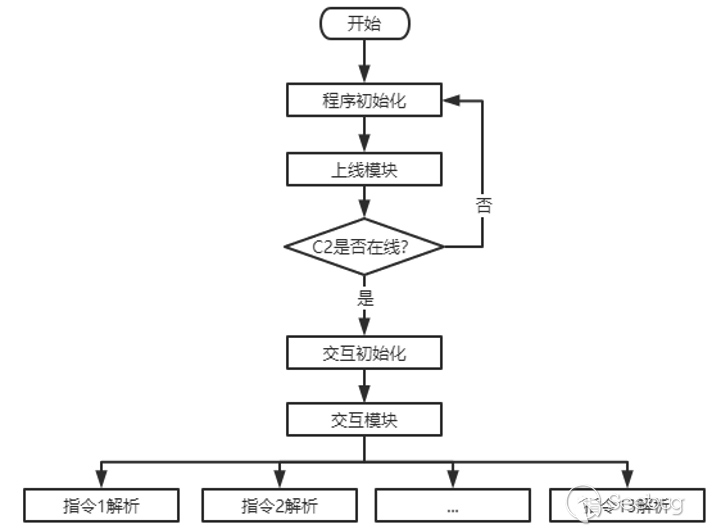
EyeShell is a .NET-based modular backdoor that interacts with a remote command-and-control (C2) server. Its functionalities include executing commands to enumerate files and directories, downloading and uploading files, executing specified files, deleting files, and capturing screenshots.
Patchwork also reportedly created a counterfeit review site for chat apps, deceptively promoting their own attacker-controlled app at the top of the list.
Another alias linked with Patchwork’s activities is ModifiedElephant, according to Secureworks. The name corresponds to attacks against human rights activists, academics, and lawyers across India, intended for long-term surveillance and planting “incriminating digital evidence” in relation to the 2018 Bhima Koregaon violence in Maharashtra.
In a parallel development, another round of phishing attacks has been identified, led by the group Bitter, targeting aerospace, military, large corporations, national government affairs, and universities in China, deploying a new backdoor named ORPCBackdoor.
Bitter, a South Asian threat actor, has previously been observed to target the nuclear energy sector in China, delivering malware via CHM and Microsoft Excel Files, designed to establish persistence and download additional payloads.
Found this news interesting? Follow us on Twitter and Telegram to read more exclusive content we post.


