A critical vulnerability within Python’s URL parsing function has come to light, opening the doors to potential arbitrary file access and the execution of unauthorized commands.
Security researchers have issued a stern warning about a high-severity flaw, assigned CVE-2023-24329 with a CVSS score of 7.5, which has been unveiled within Python’s URL parsing function. This security lapse could be manipulated to circumvent blocklisting protocols.
Should this vulnerability be successfully exploited, it has the potential to facilitate unauthorized file reads and grant the ability to execute commands without proper authorization.
According to the advisory released by the CERT Coordination Center (CERT/CC), “A vulnerability in the urllib.parse module of Python versions prior to v3.11 can be exploited by malicious actors to evade blocklisting measures by employing a URL that commences with whitespace characters. The urlparse function exhibits parsing irregularities when the entire URL initiates with such whitespace characters. This parsing anomaly affects both hostname and scheme parsing, ultimately nullifying any efficacy of blocklisting mechanisms.”
Researchers have underscored that the urlsplit() and urlparse() APIs lack input validation and might not trigger error alerts upon encountering invalid inputs.
Functioning of the Python URL parsing
The vulnerability’s exploitation hinges on the provision of a URL that commences with whitespace characters.
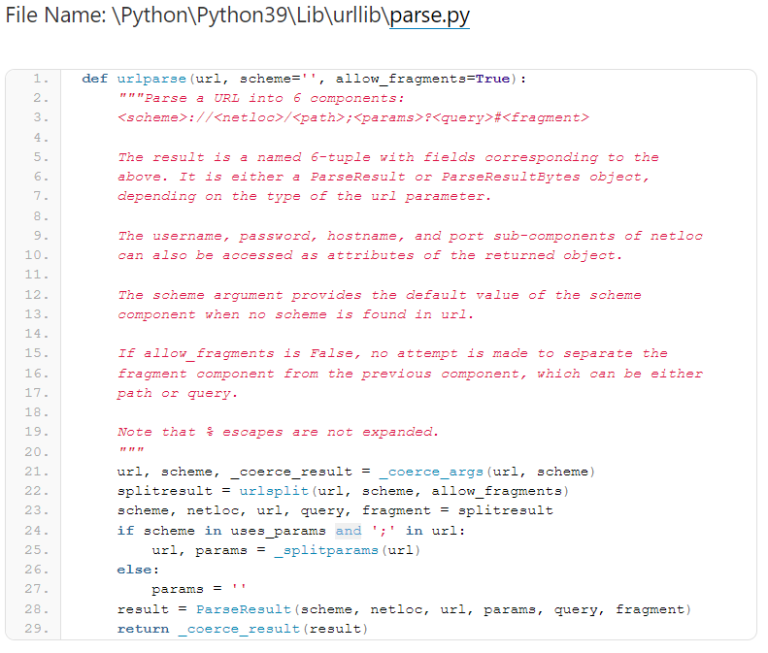
The security loophole was unearthed by Yebo Cao, a researcher, in July 2022.
Expressing the gravity of the situation, Cao commented, “In my personal opinion, this vulnerability holds significant implications due to the widespread utilization of the urlparse() library. While blocklisting might be considered suboptimal, there are numerous scenarios in which it remains a necessity.” Cao added, “This vulnerability empowers potential attackers to skirt the protections established by developers for schemes and hosts. It is conceivable that this vulnerability could significantly contribute to Server-Side Request Forgery (SSRF) and Remote Code Execution (RCE) in a diverse array of scenarios.”
Affecting all versions of Python preceding 3.11, the vulnerability has been effectively addressed in the subsequent releases:
- Version 3.12 and above
- Versions 3.11.x starting from 3.11.4
- Versions 3.10.x starting from 3.10.12
- Versions 3.9.x starting from 3.9.17
- Versions 3.8.x starting from 3.8.17
- Versions 3.7.x starting from 3.7.17
Furthermore, implementing the strip() function prior to URL processing could also serve as a potential mitigation strategy against this vulnerability.
Found this news interesting? Follow us on Twitter and Telegram to read more exclusive content we post.


