Recent investigations have highlighted a potential method that cyber attackers might employ to skilfully dodge malware detection, focusing on exploiting the Windows Container Isolation Framework.
This revelation was unveiled by Daniel Avinoam, a security researcher from Deep Instinct, during the DEF CON security summit earlier this month.
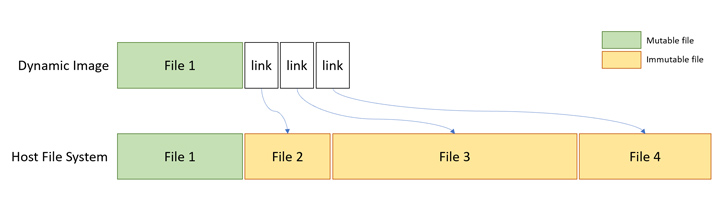
Central to Microsoft’s container design, inclusive of its Windows Sandbox, is the employment of a dynamically created image. This image acts to distinguish the file system of each container from its host while also circumventing the redundancy of system files.
Described as an “OS image that retains pristine file versions that can be altered but is linked to those that remain constant in the existing Windows image on the host,” this approach significantly reduces the need for extensive OS space.
This is where the Windows Container Isolation FS (wcifs.sys) minifilter driver becomes essential. This driver’s primary role is to maintain the filesystem demarcation between Windows containers and the main host.
The underlying concept suggests running the ongoing process within a virtual container and capitalizing on the minifilter driver to manage I/O tasks. This arrangement would allow operations like file creation, reading, writing, and deletion, all without ringing any alarms in the security software.
It’s vital to understand that a minifilter connects to the file system in a roundabout manner. It registers with the filter manager and specifies the I/O operations it intends to screen. Every minifilter is then assigned an “altitude value” by Microsoft based on its filter prerequisites and load sequence.
With an altitude range of 180000-189999 (precisely 189900), the wcifs driver operates distinctly from antivirus filters. Most of these antivirus filters operate at altitudes ranging from 320000-329999. This altitude difference means certain file operations can occur without activating their respective callbacks.
Avinoam clarified, “Thanks to our ability to modify files utilizing the IO_REPARSE_TAG_WCI_1 reparse tag without antivirus drivers detecting them, their detection process won’t get the full context, preventing any alarms from being raised.”
However, it’s important to note that this attack method demands admin rights to engage with the wcifs driver. Moreover, it doesn’t provide the leverage to modify files on the host system directly.
The revelation emerged simultaneously as the cybersecurity firm showcased a covert method named NoFilter. This strategy misuses the Windows Filtering Platform (WFP) to amplify user rights to SYSTEM levels, paving the way for potential malicious code execution.
This method enables the harnessing of WFP to clone access tokens for varied processes, stimulate an IPSec link, and exploit the Print Spooler service to embed a SYSTEM token, facilitating unauthorized system access.
Found this news interesting? Follow us on Twitter and Telegram to read more exclusive content we post.


