In a sweeping cyber assault, nearly 2,000 instances of Citrix NetScaler have fallen victim to an extensive campaign of compromise, leveraging a recently revealed critical security vulnerability. This attack has seen threat actors effectively exploit CVE-2023-3519, thereby infiltrating NetScaler ADC and Gateway servers with insidious web shells to establish enduring unauthorized access.
A detailed advisory issued by NCC Group illuminated the unfolding threat landscape, emphasizing that the attackers seem to have systematically capitalized on CVE-2023-3519, seamlessly implanting web shells on exposed NetScalers. These surreptitious implants grant the adversary the power to execute arbitrary commands even after patching and rebooting the NetScaler.
Citrix took swift action to rectify the vulnerability last month, but the repercussions of the attack persist. Shadowserver Foundation’s prior revelation of nearly 7,000 vulnerable and unpatched NetScaler ADC and Gateway instances laid the foundation for this disturbing revelation. These instances have now emerged as havens for the insidious deployment of PHP web shells, extending unauthorized remote access to attackers.
NCC Group’s meticulous analysis has unveiled that a staggering 1,828 NetScaler servers remain tainted by the intrusion, with approximately 1,248 already fortified against the vulnerability. The concerning implication here is that despite patching, these systems have not been subjected to thorough checks to detect signs of successful exploitation.
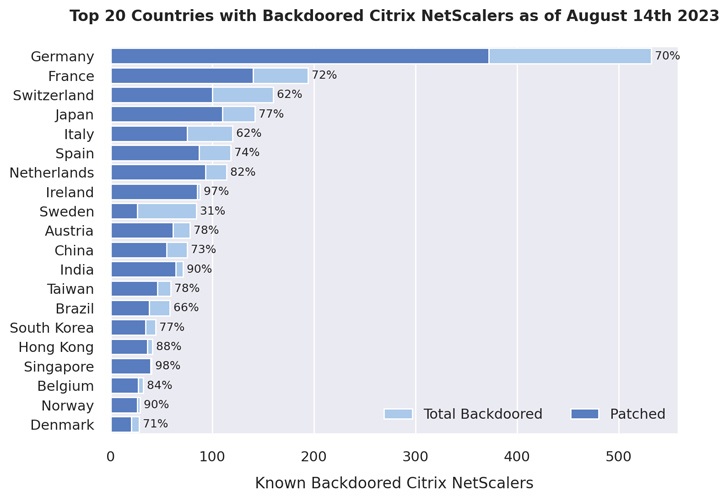
The breadth of compromise is staggering, with a total of 2,491 web shells detected across 1,952 distinct NetScaler appliances. A noteworthy geographical pattern emerges from this wave of attacks, as the bulk of affected instances are clustered in Germany, France, Switzerland, Japan, Italy, Spain, the Netherlands, Ireland, Sweden, and Austria.
Interestingly, despite Canada, Russia, and the U.S. having harbored thousands of vulnerable NetScaler servers just last month, no trace of web shells has been identified on any of these systems. This selective targeting adds a layer of intrigue to the already complex assault.
The sheer scale of the exploitation is alarming, with an estimated 6.3% of the 31,127 NetScaler instances susceptible to CVE-2023-3519 having fallen prey to this campaign by July 21, 2023.
Adding to the evolving scenario, cybersecurity firm Mandiant has introduced an open-source tool designed to empower organizations to scour their Citrix appliances for telltale signs of post-exploitation activity linked to CVE-2023-3519. This tool aims to provide a means of defense against further compromise and ensure the identification of any lingering threats.
Found this news interesting? Follow us on Twitter and Telegram to read more exclusive content we post.


