In a recent revelation, it has been disclosed that the infamous Lazarus Group, a North Korea-linked hacking organization, has laundered a staggering $900 million in cryptocurrency through cross-chain channels. This sophisticated operation, part of an estimated $7 billion in illicitly laundered cryptocurrency, unfolded between July 2022 and July of this year.
Blockchain analytics firm Elliptic, in its latest report, highlighted the rising trend of crypto crime displacement toward chain- or asset-hopping typologies, as traditional entities like mixers face seizures and sanctions scrutiny. Cross-chain crime involves the swift conversion of crypto assets from one token or blockchain to another, obscuring their origin. This method has become increasingly lucrative for money laundering and serves as an alternative to conventional approaches like mixers.
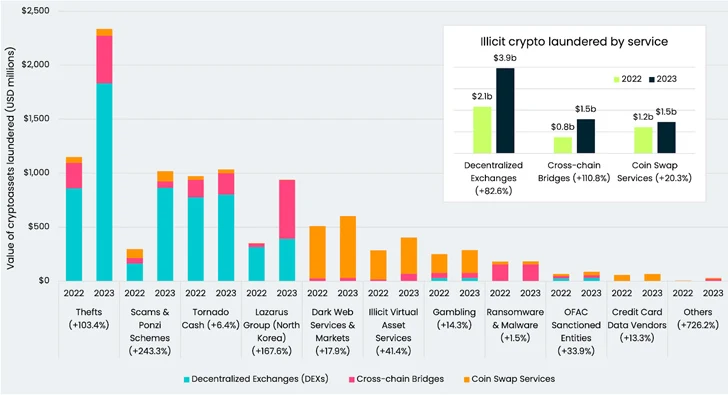
Elliptic’s data analysis revealed that the Lazarus Group extensively used cross-chain bridges, contributing significantly to the 111% surge in funds sent via such services. Since June 2023, the North Korean hacking crew has pilfered approximately $240 million in cryptocurrency through targeted attacks on platforms such as Atomic Wallet ($100 million), CoinsPaid ($37.3 million), Alphapo ($60 million), Stake.com ($41 million), and CoinEx ($31 million).
ESET, a cybersecurity firm, characterized the Lazarus Group as a multifaceted threat actor engaged in cyber espionage, cyber sabotage, and financial gain. Their diverse tactics and innovative approaches have set them apart within the cybercriminal landscape.
Moreover, the Lazarus Group has been associated with the use of Avalanche Bridge to deposit over 9,500 bitcoins, simultaneously employing cross-chain solutions to move the stolen assets. Elliptic emphasized that these transactions lacked any legitimate business purpose, indicating a clear intent to obscure their origin through tactics known as ‘chain-hopping.’
This revelation coincides with warnings from South Korea’s National Intelligence Service (NIS) about North Korea’s ongoing cyberattacks on its shipbuilding sector. The NIS revealed that North Korean hacking organizations primarily utilized tactics such as infiltrating IT maintenance companies’ computers and distributing phishing emails to internal employees to install malicious code.
The Lazarus Group’s audacious exploits underscore the evolving nature of cryptocurrency-related crimes and the urgent need for international cooperation to combat these sophisticated cyber threats effectively.
Found this news interesting? Follow us on Twitter and Telegram to read more exclusive content we post.


